TCP/IP
Hijacking is when an authorized user gains access to a genuine network
connection of another user. It is done in order to bypass the password
authentication which is normally the start of a session.
In theory, a TCP/IP connection is established as shown below −
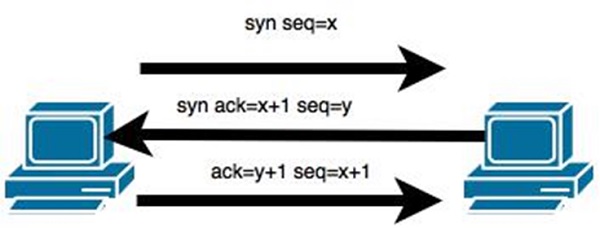
To hijack this connection, there are two possibilities −
- Find the seq which is a number that increases by 1, but there is no chance to predict it.
- The second possibility is to use the Man-in-the-Middle attack which, in simple words, is a type of network sniffing. For sniffing, we use tools like Wireshark or Ethercap.
Example
An
attacker monitors the data transmission over a network and discovers
the IP’s of two devices that participate in a connection.
When
the hacker discovers the IP of one of the users, he can put down the
connection of the other user by DoS attack and then resume communication
by spoofing the IP of the disconnected user.
Shijack
In
practice, one of the best TCP/IP hijack tools is Shijack. It is
developed using Python language and you can download it from the
following link − https://packetstormsecurity.com/sniffers/shijack.tgz
Here is an example of a Shijack command −
root:/home/root/hijack# ./shijack eth0 192.168.0.100 53517 192.168.0.200 23
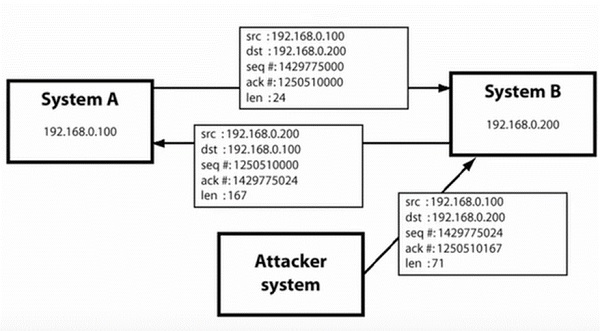
Here, we are trying to hijack a Telnet connection between the two hosts.
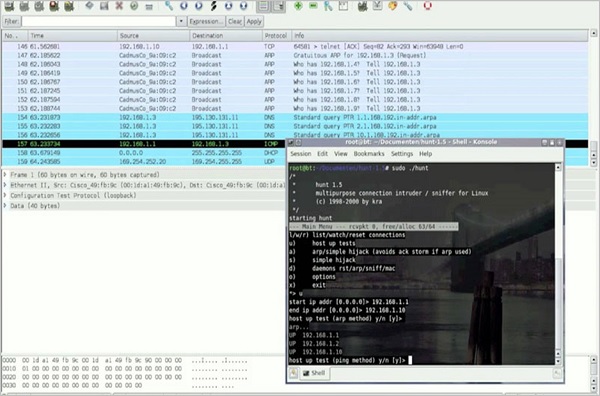
Hunt
Hunt is another popular tool that you can use to hijack a TCP/IP connection. It can be downloaded from − https://packetstormsecurity.com/sniffers/hunt/
Quick Tip
All
unencrypted sessions are vulnerable to TCP/IP session hijacking, so you
should be using encrypted protocols as much as possible. Or, you should
use double authentication techniques to keep the session secured.
No comments:
Write comments